Preparation
Need to get ClientID and ClientSecret from Funpepper platform first, and then you can do the Authorization flow called OAuth2.0.
Description of Authorization process
OAuth2.0 let third-party application get the user infomation on Funpepper, and it support the authorization_code mode which only can be used on server end.
The entire flow just like below:
User enter the third-party game page from Funpepper, then the extra parameter code will be appended to the game’s link. Developer can get the access_token from Funpepper by invoking server API width the code, ClientId, ClientSecret and other parameters. Once got access_token, developer can get all the ability we provide. Such as getting user infomation on Funpepper and doing other necessary action.
Get access_token sequence diagram:
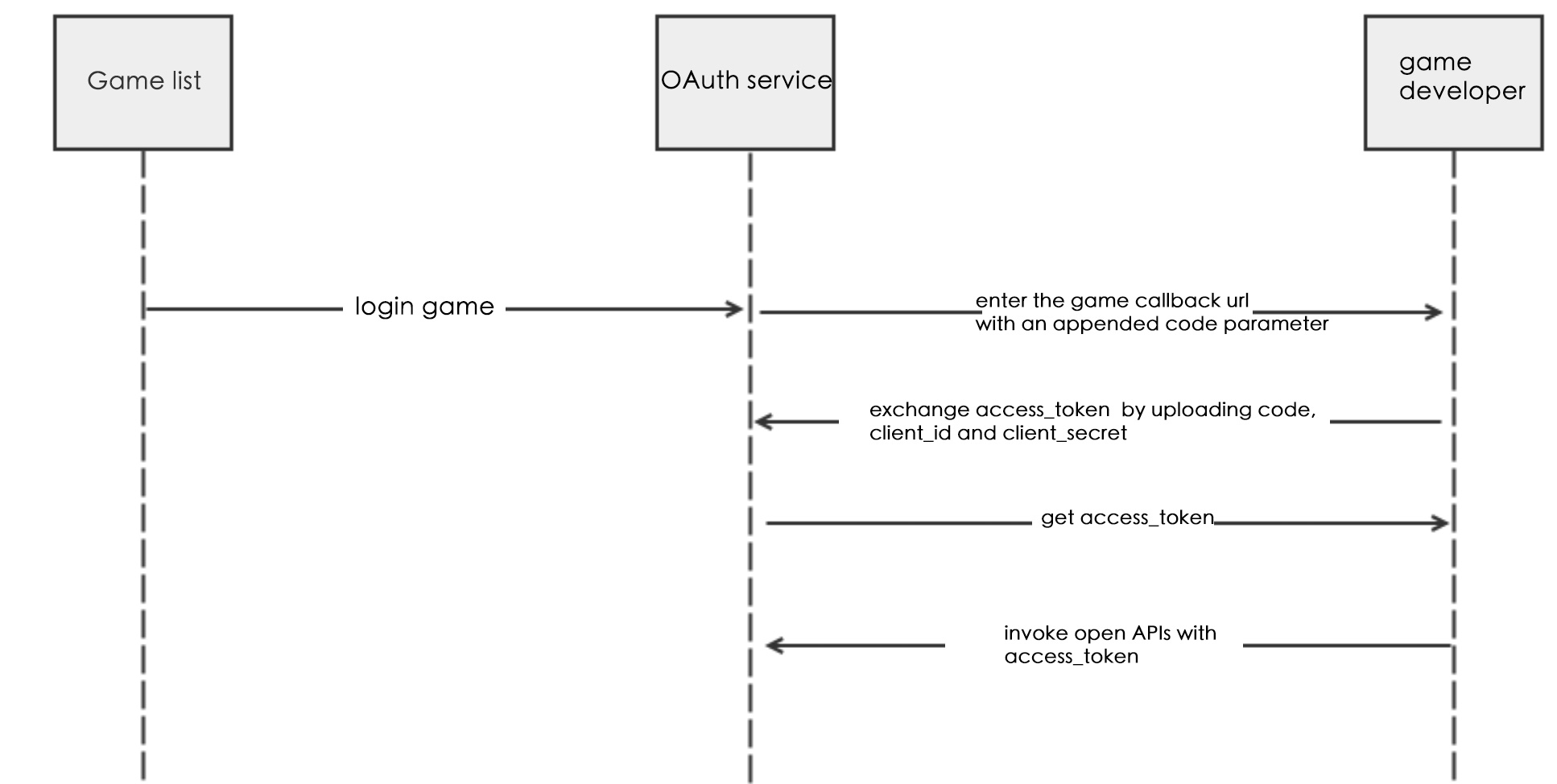
1. Open callback page width code
Every game need to configure the game’s callback link(redirect_uri), and every time the user enters the game page, Funpepper will append the extra code parameter to redirect_uri. Game developer can use the code to exchange access_token.
2. Exchange access_token through code
POST https://up-oauth.pengpengla.com/token |
Upload parameter
| Parameter | Necessary | Description |
|---|---|---|
| client_id | YES | The unique id for developer on Funpepper |
| client_secret | YES | The secret key uniquely associated with client_id |
| code | YES | The code obtained in the first step |
| grant_type | YES | The string value is fixed, ‘authorization_code’ |
| redirect_uri | YES | The callback link configured for game on Funpepper and must keep the same as in the first step. |
Response
{ |
Response description
| Parameter | Description |
|---|---|
| access_token | Voucher for invoking open APIs |
| expires_in | Voucher validity period, unit: second |
| refresh_token | This access_token that will take effect in the future, after access_token value obtained this time has expired |
| open_id | The unique of Funpepper user in application developed by developer. |
| scope | This string value is fixed, ‘SCOPE’ |
Other description
Access_token is the unique credential for invoking the open APIs on Funpepper. But the validity period of access_token (currently 12 hours) is short, refresh_token can be used to refresh the access_token after the access_token timeout. There are two kinds of access_token refresh results:
- If access_token has timed out, refresh access_token will get a new access_token and a new timeout time.
- If access_token is not timed out, refresh access_token will not change access_token, but the timeout will refresh, equivalent to the renewal of access_token. And refresh_token has a long validity period (90 days). When refresh_token expires, the user is required to re-authorize it.
3. Refresh access_token
POST https://up-oauth.pengpengla.com/token |
Upload parameter
| Parameter | Necessary | Description |
|---|---|---|
| client_id | NO | The unique id for developer on Funpepper |
| client_secret | NO | The secret key uniquely associated with client_id |
| grant_type | YES | fixed string, ‘refresh_token’ |
| refresh_token | YES | The refresh_token obtained in the first |
| redirect_uri | NO | The callback link configured for game on Funpepper and must keep the same as in the first step. |
Response
{ |
Response description
| Parameter | Description |
|---|---|
| access_token | Voucher for invoking open APIs |
| expires_in | Voucher validity period, unit: second |
| refresh_token | This access_token that will take effect in the future, after access_token value obtained this time has expired |
| open_id | The unique of Funpepper user in application developed by developer. |
| scope | Fixed string, ‘SCOPE’ |
4、Special attention
Make sure that ClientSecret and access_token are placed on the server and that the open APIs is invoked by the server-side program.
The reasons are as follows:
- client_secret is the secret key used to invoke open APIs, which may lead to high-risk consequences such as application data leakage and user data leakage of the application. So stored in the client, it is very likely to be maliciously stolen (such as decompiling to get client_secret)
- access_token is the credential (equivalent to user login state) to invoke open APIs of Funpepper. If stored on the client side, it will easily lead to user data leakage and malicious attacks on funpepper-related interfaces.
- aefresh_token is a long-term credential that authorizes third-party applications for users. It is only used to refresh access_token, but the leakage is equivalent to access_token leakage. The risk is the same as above.